What is WannaCry, WannaCrypt, WanaCrypt0r 2.0, Wanna Decryptor and how to Protect Yourself from Ransomware
WannaCry, Wanna Crypt, WannaCrypt0r 2.0 is a type of Trojan virus called ‘ransomware’, which holds the infected computer hostage until ransom is paid by the computer owner. Over the weekend (May 13-14, 2017) the world has experienced a major impact by the WannaCry ransomware attack. More than 200,000 systems across more than 150 countries were affected. The ransom was initially set to $300 in bitcoins and if not paid within three days, the amount will increase to $600. If the ransom is not paid within seven days WannaCry will delete the encrypted files.
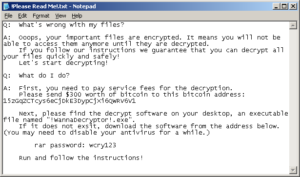
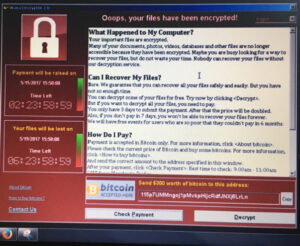 In addition to encrypting all of user files a text file is left on the user’s desktop:
In addition to encrypting all of user files a text file is left on the user’s desktop:
 How can you prevent WannaCry attack?
How can you prevent WannaCry attack?
The following steps can be taken to minimize the risk of becoming a victim:
- Backup your critical systems immediately on a separate drive or a machine. Backups are the only full mitigation against data loss due to ransomware.
- Ensure your Windows Operating System is activated with genuine product ID
- Identify internet-facing systems that have not yet been patched and updated and remediate immediately. Eliminate operating systems which are no longer supported by the vendor (e.g. Windows XP)
- Apply MS17-010 – Critical Security Update for Microsoft Windows SMB Server (4013389) on all your systems https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
- Disable SMB port (port 445) manually on your systems – by modifying your registry
- Add a rule to your router or firewall to block TCP/445 traffic from untrusted systems. If possible, block 445 inbound to all internet-facing Windows systems.
- Ensure your email filter is updated and functionally blocking dangerous email threats
- Train employees to recognize phishing emails that might contain infected links and/or documents.
What should you do if your systems have been infected?
Disconnect the infected systems from the network immediately to prevent ransomware from spreading across the network or share drives. Power off the system. According to your Incident Response plan contact your IT / Information Security department and ensure notification is distributed to other users to let them know ransomware has been detected within your organization’s network.
Contact a local field office of the Federal Bureau of Investigation (FBI) or U.S. Secret Service immediately to report the discovery of ransomware.
Paying the ransomware demand does not guarantee retrieval of your data!
The US Government does not encourage paying ransom to criminals, and paying the ransom does not guarantee retrieval of your encrypted data.
Contact Security Compliance Associates www.scasecurity.com.
We can help you identify vulnerable systems by running a thorough scan of your network. Our scanning tools have been updated to detect the WannaCry vulnerability and protect your organization against future attacks. Contact us today. Our experienced consultants are standing by.

