HIPAA Security Risk Assessment Key Points to Remember
I have been asked many times in the past few months, what constitutes a Risk Assessment? Is there a checklist I can follow? Does the tool on http://www.healthit.gov/providers-professionals/security-risk-assessment-tool guarantee compliance? Can software complete the risk assessment for me?
The answer to the last two questions above is simple. No. My goal here is to simply educate those in the healthcare field about what is out there, what is required and how to guide your practice to ensure you are protecting your ePHI.
Risk Assessment:
A thorough and comprehensive HIPAA Security Risk Assessment needs to look at your Technical, Administrative and Physical Safeguards and determine the risks, threats and vulnerabilities that exists, document those risks, determine the likelihood of that risk occurring and the impact that would have on your institution. The goal is to protect the confidentiality, integrity, and availability of electronic protected health information. This is to be part of your Risk Management Process. Your risk management process should call on you to perform these assessments as part of your regular cycle to ensure your remediation is holding up and you are addressing new risks, threats and vulnerabilities as they arise. Here is an example of what your risk management process should look like:
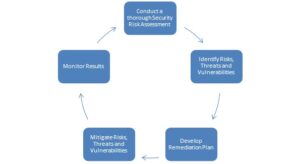 Check Lists:
Check Lists:
This has been brought up by so many people that I will not waste too much of your time on it here. Following a checklist will tell you things you need to do. Remember the milk, pick up the kids from practice, update your notice of privacy practices. However, using a checklist does not constitute a risk assessment. You must determine the risk, evaluate the likelihood of occurrence and the impact of an occurrence. A checklist will not ensure that you are aware of the risks, threats and vulnerabilities that exist in your environment.
Self-Help Tool:
The self-help tool provided on www.healthit.gov’s web page does not guarantee compliance and even has a disclaimer at the bottom of the page which reads:
“The Security Risk Assessment Tool at HealthIT.gov is provided for informational purposes only. Use of this tool is neither required by nor guarantees compliance with federal, state or local laws. Please note that the information presented may not be applicable or appropriate for all health care providers and organizations. The Security Risk Assessment Tool is not intended to be an exhaustive or definitive source on safeguarding health information from privacy and security risks. For more information about the HIPAA Privacy and Security Rules, please visit the HHS Office for Civil Rights Health Information Privacy website.
NOTE: The NIST Standards provided in this tool are for informational purposes only as they may reflect current best practices in information technology and are not required for compliance with the HIPAA Security Rule’s requirements for risk assessment and risk management. This tool is not intended to serve as legal advice or as recommendations based on a provider or professional’s specific circumstances. We encourage providers, and professionals to seek expert advice when evaluating the use of this tool.”
One may ask why put the tool out there for people to use if it does not guarantee compliance with federal, state or local laws. Notice the last sentence encouraging providers to seek expert advice when evaluating and using this tool.
Furthermore some states have more stringent regulations which go beyond what is required by HIPAA. If the state law is more comprehensive than the federal mandate, the state’s regulatory requirements must be met. An example of this is where according to state statute; you may have less time to properly report a breach than you do under HIPAA’s Breach Notification Rule.
Another area of concern is simply that the person completing the “self-help tool” assessment does not know what risks to look for or what risks actually exist at the practice. How do you rate a risk? What types of risk exists in your environment? What is the likelihood of occurrence and what will the impact be in the event that it occurs?
Software:
Software has come a long way. We can do so many things with software. Software can not complete a risk assessment for you. It cannot complete a physical walk-thru of your facility. It does not determine if you have actually set up your personnel with the appropriate privilege. It only does what you tell it to do. Remember the old adage: “Garbage in, Garbage out”. This is true with these software programs as well. It is too easy to not clearly identify what you are putting in. Just like when you ask your phone for directions “driving directions to Decatur” you may mean Georgia, but your phone may think you mean Illinois and you drive in the wrong direction for 2 hours before you realize your phone has you going in the wrong direction. Software can only do so much.
Final Thought:
A thorough and comprehensive risk assessment cannot be completed using only a checklist, or only software, or even using the “self-help” tools that float around on the internet. To paraphrase the disclaimer by healthit.gov, you should seek out risk assessment experts to ensure that you are protecting the confidentiality, integrity, and availability of electronic protected health information. Remember, the key points to a Risk Assessment are to determine the RISKS that exists, document those risks, determine the likelihood of that risk occurring and the impact that would have on your institution. After evaluating those risk, you determine the most effective way to mitigate those risk (remediation plan), correct (follow remediation plan), monitor results and reassess. I hope you find this post both educational and useful.[/vc_column_text][/vc_column][/vc_row]

